#Complex Multi-Cloud Landscape
Explore tagged Tumblr posts
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Optimize your DevSecOps approach in a complex multi-cloud landscape. Discover best practices and empowering strategies for sustainable growth.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Keep Moving Forwards, Part 34

Azriel x Reader Fic
Summary: After finally deciding to leave your abusive and manipulative mate for good, you find unexpected companionship with Azriel, the Shadowsinger of the Night Court. As you navigate the aftermath of your traumatic relationship, you struggle to understand where the mating bond went wrong and contemplate your path forward, vowing never to return to the past.
Find other parts here: Master List
To follow this fic, follow tag "Keep Moving Forwards Fic" or comment to be tagged in future parts.
Content Warning: This story contains depictions of extreme emotional manipulation and abuse, detailed descriptions of direct physical abuse, and scenes of men hunting women with implied sexual assault. Please read at your own risk.
Word Count: 2.4K
Author's Note: This is a multi-part series. Unlike my previous works, this fanfiction delves deeper than just fluff, exploring complex emotional landscapes. As I navigate this new writing journey, I kindly ask for gentle feedback. The topics addressed are profoundly impactful, touching many lives with diverse experiences. Please be gentle with yourselves and others. Healing is a journey, and everyone processes it differently. Be kind to yourself. Take what resonates, and leave what doesn’t.
Please continue reading, being aware of the above content warnings, ensuring you are in a healthy headspace. Give yourself time to process and be gentle with yourself.
Nesta had resolutely decided to tell Cassian about the pregnancy the next time he was home. She repeated it to you so often that it seemed more a reminder to herself than a note to you. However, when Cassian returned the following week, it was painfully clear that she was having more than a little trouble letting the secret out. Worse yet were Nesta’s increasingly obvious efforts to avoid being alone with Cassian at all. She was like a cat with a bellyful of secrets, her stormy grey eyes betraying the guilt gnawing at her from within.
You reminded yourself that it was Nesta’s news to share, and she would do it in her own time. It wasn’t your place to push her, especially after your revelation had left her visibly shaken.
Since then, Nesta had taken up wearing stronger perfumes, presumably to mask any new maternal scent that might be emanating from her. Watching her test out and purchase scents that most shopkeepers admitted they hadn't sold much of due to their rather potent odors was almost comical. She doused herself in them anyway. The first night Cassian was home, the perfume had been a particularly strong mix of lavender and something else you couldn’t quite place, and it left you wondering if she had actually used over half the bottle.
That same night, Nesta expertly managed to avoid dinner altogether, claiming an urgent meeting with a court advisor. The only urgency in her voice, however, was to avoid Cassian’s probing questions and comments regarding her new musk, which he described as, “worse than a scouting party that had been out in the woods for three weeks with no access to running water.”
Knowing his habits, she waited until he had passed out on the couch, snoring away, his wings sprawled wide, and his hulking body draped over the fine velvet. Azriel, perched next to you looking over a few documents Cassian had brought back from his trip, remarked that he looked like a dragon hoarding the pile of cushions he had positioned under himself.
It was only then that Nesta tiptoed past the living room door, where you sat in front of the fire, sitting on the floor in front of Azriel, curled up with a book. She moved like one of Azriel’s shadows, despite the perfume cloud that announced her arrival far before her actual body. You glanced up at her, catching her eye as she attempted to sneak past. Your eye caught hers as you smiled, amused and also sympathetic. Her return smile was tight-lipped, full of guilt and more than a little sheepishness. The kind of look that said, “Yes, I know, I’m being ridiculous, but please don’t say anything.”
Your book lay forgotten in your lap as you watched her. It was like witnessing a young fae sneaking back in after curfew. Her expression softened as you gave a tiny nod, a silent message: “Take your time. It’s okay.”
Nesta took a few more calculated steps forward, just out of earshot, before Azriel, without looking up from his papers, asked, “So, what’s all that about?”
His voice spooked you enough that you jumped lightly in your seat. “What?” you replied a bit too quickly, trying to hide your guilt by burying your nose deeper into your book.
Azriel’s eyes remained on his papers, but there was a teasing note in his voice. “Nesta’s sneaking around. And you two are giving each other these...glances.”
“You know, I don’t appreciate the parts of you that notice everything. You’re too nosy,” you quipped, hoping to deflect.
He simply shrugged. “It’s my job.”
You mulled over your options, finally settling on, “It’s not my place to say.”
Azriel folded down one corner of his page, glancing at you with those perceptive hazel eyes. “Is everything okay between her and Cassian?”
“I’m not telling you anything,” you muttered, your eyes glued to the page where the words blurred together, unread.
Setting his papers aside, Azriel slid down off the couch, drawing his knees to his chest as he sat next to you. He tried to catch your gaze, but you chewed your bottom lip, pretending to be engrossed in the book. After a few moments of awkward silence, you peeked at him from the corner of your eye. “Can I help you?” you asked, more to break the tension than anything else.
Azriel chuckled softly, his thumb grazing his nose. “What?” you pressed, shutting the book a bit too loudly. Cassian stirred lightly, a bit of drool hitting the floor. Nesta would have woken him immediately to make him clean it, but Azriel just watched as Cassian rolled over, now facing the back of the couch.
Lowering his voice to a whisper, Azriel said, “You know too?”
You turned to him, trying to mask your guilt with wide eyes. “Know what?”
“That Nesta’s—” He mimed an enlarged stomach with his hands.
Your mouth dropped open, struggling to find the right words. “How did you—? Did she—?”
Azriel shook his head, glancing back at Cassian. “It’s not hard to deduce. She’s acting strange. Avoiding him, and he’s not desperately trying to win her back for something he did. Plus, those perfumes are terrible. Nesta has much better taste.”
You let out a breath of relief. “Thank the gods someone else knows.”
“She hasn’t told him yet?” he asked, eyebrows knitting together.
You shook your head. “I just guessed it last week.” You gestured to the sleeping figure across the room. “How has he not noticed?”
Azriel shrugged, the corners of his mouth twitching. “I’d like to say it’s because he’s been away and tired, but honestly, that’s giving him too much credit.”
Cassian choked on a snore, readjusting himself again.
Azriel’s expression grew more serious. “Why hasn’t she said anything?”
You set the book on the floor beside you. “She’s worried about getting his hopes up. They’ve had trouble the last few times.”
Azriel nodded slowly, his eyes darkening with unspoken memories. You hesitated before asking the question weighing heavily on your mind. “How many babes have they lost?”
Azriel’s brows drew together, his eyes clouding with sadness. “I think four. Three that Cassian knows about.”
Your stomach churned. “How do you know about the other one?”
Azriel leaned back, resting his head on the cushion behind him, his gaze fixed on the ceiling. “She didn’t come to training one morning. Cassian was out on some mission for Rhys. Gwyn and I found her in the bathing room, just lying on the floor. She hadn’t told any of us about the babe.”
You watched the light in his eyes fade, replaced by a sorrowful reflection. “You didn’t tell Cassian?”
Azriel shook his head, the cushion shifting under him. “Nesta begged us not to. It didn’t feel right for me to tell him.”
Your gaze shifted to Cassian, sprawled on the couch, always the first to approach children wherever you went. He loved babysitting for Feyre and Rhys, encouraging them to extend their trips so he could spend more time with Nyx. He tossed Nyx higher into the air than anyone else, making Nesta gasp and scold him. Cassian was a natural with children, yet he never mentioned wanting his own. Perhaps he didn’t want to pressure Nesta. Or maybe he was trying to accept that he might only be an uncle, never a father.
The following night, you normally found yourself eagerly anticipating the weekly gathering at the River House. Those evenings were a balm to your soul, leaving you with a full belly, cheeks aching from smiling, and a heart warmed by laughter. But tonight, a subtle tension lingered as Azriel and Cassian flew you and Nesta down towards the High Lord and Lady’s home. Nesta’s tight-lipped expression as she gazed out over the sparkling Sidra was all you could seemingly focus on. Cassian, oblivious, chattered away to Azriel, but you were too preoccupied with Nesta’s silence to catch much of their conversation.
When you finally landed on the lawn, Elain and Lucien arrived behind you, hand in hand. Azriel placed a comforting hand on your back, his thumb rubbing up and down soothingly as he leaned down to whisper, “She’ll tell him.”
You swallowed your anxiety and nodded, falling in step with the group as you approached the door. It creaked open, revealing a tiny pair of hands tugging at the large oak door. A more slender hand appeared above them, helping to pull it open. Nyx’s shining, pudgy face peeked out, bathed in the warm faelight from inside. Without hesitation, he sprinted out towards the group, his bare feet pattering against the stones as Feyre’s voice called after him, “Nyx, no! You didn’t put shoes on!”
Nyx whipped his head back towards his mother, his eyes wide with defiance as he assessed the situation. Feyre’s arms crossed, her lips tightening into a stern line as she prepared to bring down the hammer. Caught between the allure of Cassian, Nyx’s obvious favorite among all of you, and the impending scolding, the little warrior made a split-second decision and bounded towards Cassian, who dropped into a crouch, arms outstretched.
Feyre scoffed, her eyes rolling as she cast a resigned smile at the group. Cassian scooped Nyx up, hoisting him over his shoulder like a sack of potatoes. Nyx’s giggles filled the air.
As Cassian approached the front door, Nesta trailed behind, running a loving hand through her nephew’s jet-black hair. She licked her thumb and attempted to rub off some paint from his forehead. “I believe this belongs to you,” Cassian announced, shifting Nyx on his broad shoulder as the boy giggled again.
“Oh no,” Feyre replied with mock seriousness, her voice laced with humor, “My little boy wouldn’t go running out without his shoes on. And this one seems to be completely bare.” She tickled the soles of Nyx’s feet, causing him to squirm and kick lightly at Cassian’s chest as he laughed.
“So can I keep him?” Cassian asked, eyes twinkling mischievously.
“No!” Nyx howled, still trying to stifle his laughter. “I’m not yours!” he cried out, wriggling in Cassian’s hold.
Cassian dropped Nyx back to the floor with a feigned grunt. “Then you better start listening to your mama, or she might just let me take you.”
Nyx darted past Feyre, who sighed and shook her head as he pushed into her slightly, knocking her off balance. Even though Nyx barely came up to her knee, it was very clear he had both the most powerful fae in the Night Court wrapped around his tiny chubby finger. She rolled her eyes again and turned back to Cassian, bringing him into an embrace. “I swear, he’s getting more like you every day.”
Cassian pulled back with a grin, pecking her on the cheek. “Well, you’re welcome for encouraging him to be such a fun-loving, hilarious child.”
Nesta stepped in, gently nudging Cassian aside to hug her sister as Feyre replied, “Cassian, I’m not sure if you ever grew out of your terrible twenties.”
Cassian brushed past her with a laugh, following Nyx’s excited calls from the sitting room.
The evening began as it typically did. Feyre was curled up against Rhys on one of the sitting room sofas, their casual intimacy still striking you as refreshingly normal despite their lofty positions. Elain disappeared into the kitchen, determined to help with dinner preparations, though Feyre protested that everything was already prepared. Nesta sat gracefully in one of the wingback chairs, her face resting in her palm as she observed Cassian on the floor. Nyx clambered over him like a piece of furniture, occasionally running out of the room to fetch another toy for his uncle to play with.
You and Azriel sat opposite, each in your own chair, cautious about displaying affection in front of others. Though you were certain everyone, save for Nyx, was aware of your slowly blossoming relationship, neither of you felt comfortable being overt.
At the dinner table, Nesta’s unusual quietness became more apparent. She moved her food around her plate, barely looking up as Cassian, Rhys, and Azriel guffawed over something. Elain, Feyre, and Lucien were engrossed in a discussion about a new playhouse opening in the city, occasionally trying to draw you into the conversation. However, your attention kept drifting to Nesta, who seemed to be retreating into herself.
Nyx, having finished his dinner, climbed down from his chair despite Feyre’s admonishments to stay put. He crawled under the table and tugged on Cassian’s pant leg, pleading to be lifted into his lap. Cassian, ever the doting uncle, obliged, and spent the rest of the meal eating around the tiny wings of his nephew. Nyx’s laughter filled the room as he and Cassian played a simple game—Nyx straining to unfurl Cassian’s massive fingers clenched into a fist. You couldn’t help but notice the small, almost wistful smile that flickered on Nesta’s lips as she watched the two of them—the first you’d seen since Cassian returned.
Then, amidst the overlapping conversations, Nesta’s voice cut through. “Rhys, Feyre, can Cassian and I borrow the cabin this weekend?”
The room fell silent, all eyes turning to Nesta. It was the first substantial thing she had said all evening, and everyone seemed to realize it at once.
“Of course,” Feyre replied smoothly, taking another sip of her wine.
Cassian, taken aback, glanced at Nesta. “I didn’t know you wanted to go this weekend.”
Nesta shrugged, her fork chasing a rogue piece of meat. “I just think it would be nice to get away for a few days. Especially since you’ve been gone.”
Nyx, seizing the moment where Cassian had lost focus, gave a triumphant shout, “I did it!” He quickly turned back to his nephew, his fingers indeed loosened, praising him with genuine enthusiasm.
You caught Nesta’s eye across the table, and she exhaled a small sigh of relief as she took what might have been her first real bite of the evening. She offered you a tentative smile.
Azriel’s hand found your knee under the table, squeezing gently, a silent acknowledgment of the shared relief.
You turned towards him to say something, but his expression stopped you. He was smiling at you with a glimmer in his eyes, a teasing excitement that you couldn’t quite decipher. His eyes sparkled with a mischievous light.
You tilted your head, puzzled, silently questioning him. Azriel merely arched his brows, a playful challenge in his gaze, and took a leisurely sip of his wine. He turned back to the conversation with Cassian and Rhys at the other end of the table, but not before you caught the unmistakable twinkle of anticipation in his eyes.
The look was new, something you hadn’t seen from Azriel before. It sent a swarm of butterflies fluttering in your stomach, the sudden flurry of emotion making your pulse quicken.
You felt your cheeks warm and something warm igniting in your core.
Ladies, men & my non-binary friends, we're heading into the moment we've all been waiting for: @thatacotargirl @mcuamerica @lilah-asteria @florabelll @marvelbros-oneshots @mariahoedt @quinzzelx @romantasyreader28 @minnieoo @mysteriouslydeafeningwerewolf @annabethgranger123 @krowiathemythologynerd @caroline-books @slytherintaco @sevikas-whore @sidthedollface2 @sleepylunarwolf @acourtofbatboydreams @quiettuba @julesofvolterra @darling006 @loglady00 @caninnes
#azriel x reader#azriel x you#azriel fanfiction#azriel fanfic#azriel angst#azriel x y/n#acotar fanfiction#acotar reader fic#acotar fandom#Keep Moving Forwards Fic#acotar slow burn#azriel slow burn#acotar fic#acotar reader insert#acotar reader imagine
92 notes
·
View notes
Text
The AWS Advantage: Exploring the Key Reasons Behind Its Dominance
In the ever-evolving landscape of cloud computing and web services, Amazon Web Services (AWS) has emerged as a true juggernaut. Its dominance transcends industries, making it the preferred choice for businesses, startups, and individuals alike. AWS's meteoric rise can be attributed to a potent combination of factors that have revolutionized the way organizations approach IT infrastructure and software development. In this comprehensive exploration, we will delve into the multifaceted reasons behind AWS's widespread popularity. We'll dissect how scalability, reliability, cost-effectiveness, a vast service portfolio, unwavering security, global reach, relentless innovation, and hybrid/multi-cloud capabilities have all played crucial roles in cementing AWS's position at the forefront of cloud computing.

The AWS Revolution: Unpacking the Reasons Behind Its Popularity:
1. Scalability: Fueling Growth and Flexibility AWS's unparalleled scalability is one of its defining features. This capability allows businesses to start with minimal resources and effortlessly scale their infrastructure up or down based on demand. Whether you're a startup experiencing rapid growth or an enterprise dealing with fluctuating workloads, AWS offers the flexibility to align resources with your evolving requirements. This "pay-as-you-go" model ensures that you only pay for what you use, eliminating the need for costly upfront investments in hardware and infrastructure.
2. Reliability: The Backbone of Mission-Critical Operations AWS's reputation for reliability is second to none. With a highly resilient infrastructure and a robust global network, AWS delivers on its promise of high availability. It offers a Service Level Agreement (SLA) that guarantees impressive uptime percentages, making it an ideal choice for mission-critical applications. Businesses can rely on AWS to keep their services up and running, even in the face of unexpected challenges.
3. Cost-Effectiveness: A Game-Changer for Businesses of All Sizes The cost-effectiveness of AWS is a game-changer. Its pay-as-you-go pricing model enables organizations to avoid hefty upfront capital expenditures. Startups can launch their ventures with minimal financial barriers, while enterprises can optimize costs by only paying for the resources they consume. This cost flexibility is a driving force behind AWS's widespread adoption across diverse industries.
4. Wide Range of Services: A One-Stop Cloud Ecosystem AWS offers a vast ecosystem of services that cover virtually every aspect of cloud computing. From computing and storage to databases, machine learning, analytics, and more, AWS provides a comprehensive suite of tools and resources. This breadth of services allows businesses to address various IT needs within a single platform, simplifying management and reducing the complexity of multi-cloud environments.
5. Security: Fortifying the Cloud Environment Security is a paramount concern in the digital age, and AWS takes it seriously. The platform offers a myriad of security tools and features designed to protect data and applications. AWS complies with various industry standards and certifications, providing a secure environment for sensitive workloads. This commitment to security has earned AWS the trust of organizations handling critical data and applications.
6. Global Reach: Bringing Services Closer to Users With data centers strategically located in multiple regions worldwide, AWS enables businesses to deploy applications and services closer to their end-users. This reduces latency and enhances the overall user experience, a crucial advantage in today's global marketplace. AWS's global presence ensures that your services can reach users wherever they are, ensuring optimal performance and responsiveness.
7. Innovation: Staying Ahead of the Curve AWS's culture of innovation keeps businesses at the forefront of technology. The platform continually introduces new services and features, allowing organizations to leverage the latest advancements without the need for significant internal development efforts. This innovation-driven approach empowers businesses to remain agile and competitive in a rapidly evolving digital landscape.
8. Hybrid and Multi-Cloud Capabilities: Embracing Diverse IT Environments AWS recognizes that not all organizations operate solely in the cloud. Many have on-premises infrastructure and may choose to adopt a multi-cloud strategy. AWS provides solutions for hybrid and multi-cloud environments, enabling businesses to seamlessly integrate their existing infrastructure with the cloud or even leverage multiple cloud providers. This flexibility ensures that AWS can adapt to the unique requirements of each organization.

Amazon Web Services has risen to unprecedented popularity by offering unmatched scalability, reliability, cost-effectiveness, and a comprehensive service portfolio. Its commitment to security, global reach, relentless innovation, and support for hybrid/multi-cloud environments make it the preferred choice for businesses worldwide. ACTE Technologies plays a crucial role in ensuring that professionals can harness the full potential of AWS through its comprehensive training programs. As AWS continues to shape the future of cloud computing, those equipped with the knowledge and skills provided by ACTE Technologies are poised to excel in this ever-evolving landscape.
7 notes
·
View notes
Text
Pioneering the Next Era: Envisioning the Evolution of AWS Cloud Services
In the fast-paced realm of technology, the future trajectory of Amazon Web Services (AWS) unveils a landscape rich with transformative innovations and strategic shifts. Let's delve into the anticipated trends that are set to redefine the course of AWS Cloud in the years to come.

1. Surging Momentum in Cloud Adoption:
The upward surge in the adoption of cloud services remains a pivotal force shaping the future of AWS. Businesses of all sizes are increasingly recognizing the inherent advantages of scalability, cost-effectiveness, and operational agility embedded in cloud platforms. AWS, positioned at the forefront, is poised to be a catalyst and beneficiary of this ongoing digital transformation.
2. Unyielding Commitment to Innovation:
Synonymous with innovation, AWS is expected to maintain its reputation for introducing groundbreaking services and features. The future promises an expansion of the AWS service portfolio, not merely to meet current demands but to anticipate and address emerging technological needs in a dynamic digital landscape.
3. Spotlight on Edge Computing Excellence:
The spotlight on edge computing is intensifying within the AWS ecosystem. Characterized by data processing in close proximity to its source, edge computing reduces latency and facilitates real-time processing. AWS is slated to channel investments into edge computing solutions, ensuring robust support for applications requiring instantaneous data insights.
4. AI and ML Frontiers:
The forthcoming era of AWS Cloud is set to witness considerable strides in artificial intelligence (AI) and machine learning (ML). Building upon its legacy, AWS is expected to unveil advanced tools, offering businesses a richer array of services for machine learning, deep learning, and the development of sophisticated AI-driven applications.
5. Hybrid Harmony and Multi-Cloud Synergy:
Flexibility and resilience drive the ascent of hybrid and multi-cloud architectures. AWS is anticipated to refine its offerings, facilitating seamless integration between on-premises data centers and the cloud. Moreover, interoperability with other cloud providers will be a strategic focus, empowering businesses to architect resilient and adaptable cloud strategies.

6. Elevated Security Protocols:
As cyber threats evolve, AWS will heighten its commitment to fortifying security measures. The future holds promises of advanced encryption methodologies, heightened identity and access management capabilities, and an expanded array of compliance certifications. These measures will be pivotal in safeguarding the confidentiality and integrity of data hosted on the AWS platform.
7. Green Cloud Initiatives for a Sustainable Tomorrow:
Sustainability takes center stage in AWS's vision for the future. Committed to eco-friendly practices, AWS is likely to unveil initiatives aimed at minimizing the environmental footprint of cloud computing. This includes a heightened emphasis on renewable energy sources and the incorporation of green technologies.
8. Tailored Solutions for Diverse Industries:
Acknowledging the unique needs of various industries, AWS is expected to craft specialized solutions tailored to specific sectors. This strategic approach involves the development of frameworks and compliance measures to cater to the distinctive challenges and regulatory landscapes of industries such as healthcare, finance, and government.
9. Quantum Computing Integration:
In its nascent stages, quantum computing holds transformative potential. AWS may explore the integration of quantum computing services into its platform as the technology matures. This could usher in a new era of computation, solving complex problems that are currently beyond the reach of classical computers.
10. Global Reach Amplified:
To ensure unparalleled service availability, reduced latency, and adherence to data sovereignty regulations, AWS is poised to continue its global infrastructure expansion. This strategic move involves the establishment of additional data centers and regions, solidifying AWS's role as a global leader in cloud services.
In summary, the roadmap for AWS Cloud signifies a dynamic and transformative journey characterized by innovation, adaptability, and sustainability. Businesses embarking on their cloud endeavors should stay attuned to AWS announcements, industry trends, and technological advancements. AWS's commitment to anticipating and fulfilling the evolving needs of its users positions it as a trailblazer shaping the digital future. The expedition into the future of AWS Cloud unfolds a narrative of boundless opportunities and transformative possibilities.
2 notes
·
View notes
Text
Secure Your Hybrid Cloud with Windows Server 2022 Standard
Building a Fortress: The Future of Hybrid Cloud Security with Windows Server 2022
In today's rapidly evolving digital landscape, securing your hybrid cloud environment is more critical than ever. Windows Server 2022 Standard emerges as a robust foundation, blending innovative security features with flexible management capabilities to empower businesses of all sizes. This powerful server OS is designed to meet the complex demands of modern IT infrastructure, ensuring your data remains protected while maintaining seamless connectivity across on-premises and cloud environments.
One of the standout features of Windows Server 2022 Standard is its secured-core server capabilities. This technology integrates hardware, firmware, and software security measures to create a resilient fortress against cyber threats. By leveraging features like Secure Boot, hardware root of trust, and virtualization-based security, organizations can significantly reduce the attack surface and safeguard critical assets from malicious intrusions.
Furthermore, Windows Server 2022 enhances multi-layer security through advanced threat protection mechanisms. It offers improved encryption protocols, real-time security monitoring, and streamlined patch management, enabling IT teams to identify vulnerabilities and respond swiftly to emerging threats. This comprehensive security approach ensures that your hybrid cloud remains resilient against increasingly sophisticated cyberattacks.
Managing hybrid environments has never been easier thanks to the improved hybrid server management tools integrated into Windows Server 2022. The platform provides a unified management experience, allowing administrators to control both on-premises and cloud resources efficiently. Features like Azure Arc integration facilitate seamless deployment, monitoring, and updating of servers across diverse environments, reducing operational complexity and boosting productivity.
For organizations leveraging containerization, Windows Server 2022 offers significant improvements in windows containers. Enhanced support for Kubernetes, improved isolation, and faster container startup times help developers deploy applications swiftly and securely. This ensures that your development pipeline remains agile and responsive to market needs, all while maintaining a high level of security.
Investing in the right licensing is crucial to unlock the full potential of Windows Server 2022 Standard. For competitive pricing and licensing options, explore the windows server 2022 standard license price. This license provides the essential features needed to build a secure, scalable, and efficient hybrid cloud environment.
In conclusion, Windows Server 2022 Standard is more than just an operating system; it’s a strategic enabler for modern enterprises aiming to harness the power of hybrid cloud while maintaining the highest security standards. Embrace this innovative platform to future-proof your IT infrastructure, safeguard your data, and empower your business to thrive in a digital-first world.
0 notes
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
Achieve seamless DevSecOps integration in complex multi-cloud scenarios. Leverage best practices and strategic approaches for enhanced outcomes.
#Complexities Of Multi-Cloud#Multi-Cloud Environments#Complex Multi-Cloud Landscape#Benefits Of Multiple Cloud Service Providers#Secure DevSecOps Framework#Robust DevSecOps Framework#Software Development Lifecycle#Cloud-Native Security Practices#Software Product Design And Development Solutions Company#Custom Software Product Engineering Services Company
0 notes
Text
From CAD to Cut in 48 Hours – Is On-Demand CNC Finally Delivering?
In the race to reduce production timelines, “from CAD to cut in 48 hours” has become more than just a tagline — it’s the new benchmark in modern manufacturing. CNC (Computer Numerical Control) machining has long been trusted for precision, but the surge in on-demand manufacturing services has raised expectations. Can CNC providers truly deliver at this pace without compromising on quality, complexity, or cost? In this blog, we examine how the CNC landscape is evolving to meet these demands, identify potential risks, and discuss how businesses can strike a balance between speed and performance.
The Rise of Rapid CNC Machining
Speed has always been a competitive advantage in manufacturing. But today, the pressure is not only to produce quickly — it’s to deliver high-precision, production-ready parts in a matter of hours. Thanks to digital manufacturing platforms, what once took weeks can now be done in days or even less. Here’s what’s driving this acceleration:
1. Digitally Integrated Workflows
The shift from traditional machining to digitally enabled production workflows has been instrumental. CAD files can now be uploaded directly into production pipelines, with instant quoting, toolpath generation, and even materials sourcing streamlined through software platforms. This eliminates manual intervention, reduces lag, and supports automated job scheduling for maximum efficiency.
2. Advanced CNC Equipment and Automation
Next-generation CNC machines now feature automated tool changers, live monitoring systems, and self-calibrating spindles. This allows manufacturers to run complex jobs with less operator intervention and fewer pauses between steps. These machines are also capable of multi-axis movements, allowing for the handling of more intricate geometries in a single setup, which further saves time.
3. Cloud Manufacturing and Localised Production
With cloud-based manufacturing networks and distributed production hubs, CNC machining has become more decentralised. Businesses can route jobs to the nearest or fastest available facility, thereby reducing transport lead times and enabling responsive adjustments to production. This is particularly useful for companies operating in fast-moving sectors such as medical devices or consumer electronics.
This blog is originally published here: https://quickparts.com/gb/from-cad-to-cut-in-48-hours-is-on-demand-cnc-finally-delivering/
0 notes
Text
Next-Gen Security Testing Services Using AI: A Deep Dive

In the ever-evolving landscape of software development, security breaches have grown more frequent and sophisticated. Traditional testing methods, though foundational, are no longer sufficient in identifying and addressing the fast-moving threats facing modern systems. This is where Next-Gen Security Testing Services come into play, blending AI innovation with robust testing protocols.
At Robotico Digital, we’ve redefined how security integrates into software engineering by embedding Artificial Intelligence (AI) into our advanced Security Testing Services. This deep dive explores how AI transforms Security Testing in Software Testing, enabling faster detection, smarter remediation, and continuous protection across development pipelines.
The Shift Toward AI in Security Testing
Historically, Security Testing Services were heavily reliant on manual reviews, rule-based scanners, and time-intensive penetration testing. While still valuable, these methods struggle to keep up with:
lRapid DevOps cycles
lEvolving attack vectors
lIncreasing application complexity
lHybrid cloud and microservices infrastructure
AI, specifically through machine learning (ML), Natural Language Processing (NLP), and behavioral analytics, has introduced a transformative layer of intelligence to these services. It allows security testers and developers to go beyond reactive defenses—identifying risks proactively and at scale.
How AI Enhances Security Testing in Software Testing
Incorporating AI into Security Testing in Software Testing provides multi-dimensional improvements across efficiency, accuracy, and adaptability. Let’s break down the core components.
1. Automated Vulnerability Detection
AI-powered scanners can crawl source code, binary files, API endpoints, and web interfaces to detect anomalies that indicate vulnerabilities. Unlike traditional scanners, AI engines learn from past vulnerabilities and global threat databases to continually improve detection precision.
Key Features:
lPattern recognition across massive codebases
lZero-day threat detection using anomaly detection models
lAuto-mapping of application attack surfaces
2. Adaptive Risk Prioritization
One major challenge in Security Testing Services is managing false positives and prioritizing true threats. AI models rank vulnerabilities based on:
lExploitability
lBusiness impact
lData sensitivity
lThreat intelligence feeds
This reduces alert fatigue and ensures engineering teams focus on high-priority issues first.
3. Dynamic Threat Modeling
AI systems can automatically generate and update threat models for evolving software architectures. By simulating attacker behavior, AI enables predictive testing—discovering how vulnerabilities might be chained or escalated.
4. Self-Learning Penetration Testing
AI agents mimic ethical hackers using reinforcement learning. These bots evolve through trial and error, discovering unconventional paths to exploitation and mimicking real-world attack tactics.
Robotico Digital’s AI-Powered Security Testing Stack
At Robotico Digital, we’ve built a proprietary AI-enhanced testing framework designed to deliver intelligent, continuous, and scalable security coverage. Here's what powers our next-gen Security Testing Services:
AI-Powered SAST & DAST Engines
SAST (Static Application Security Testing): Our AI models review code for insecure functions, misconfigurations, and data flow leaks at the source level.
DAST (Dynamic Application Security Testing): AI crawlers test running applications by simulating user behavior and injecting payloads to trigger security vulnerabilities.
Machine-Learning Vulnerability Correlation
We reduce redundant findings by merging results from multiple tools and identifying duplicate alerts. ML models group similar issues, track them across builds, and learn from developer remediation behavior.
AI-Based Compliance Validation
Robotico Digital uses AI to ensure compliance with:
lOWASP Top 10
lGDPR / HIPAA / PCI DSS
lNIST and ISO 27001 We map discovered vulnerabilities to these frameworks, highlighting gaps in your security and compliance posture.
Use Cases of AI in Security Testing Services
Web & Mobile Application Testing
AI identifies issues such as insecure authentication, broken access controls, and injection attacks. It tests logic errors and parameter tampering based on how real users interact with the app.
API Security Testing
APIs are high-value targets. Our AI models analyze OpenAPI/Swagger specs, apply fuzzing techniques, and test for broken object-level authorization (BOLA) and mass assignment vulnerabilities.
Cloud & Infrastructure Testing
For cloud-native applications, AI detects misconfigurations in IAM roles, storage permissions, and network security groups—especially in multi-cloud environments like AWS, Azure, and GCP.
DevSecOps Pipeline Integration
Robotico Digital integrates AI-based scanning tools directly into CI/CD platforms like GitLab, Jenkins, and Azure DevOps. This ensures shift-left security with automated gates at every build stage.
Implementation Challenges & Considerations
While the benefits are substantial, integrating AI into Security Testing Services is not without hurdles:
1. Data Quality & Training Bias
AI models require high-quality, labeled data to function accurately. Poor or biased training datasets can lead to both false positives and false negatives.
2. Explainability & Developer Trust
“Black-box” decisions from AI can frustrate developers. Robotico Digital addresses this by using explainable AI (XAI) models that provide root cause analysis and remediation context.
3. AI Model Drift
Security threats evolve. AI models must be updated regularly to avoid “drift” that could miss emerging threats. We maintain continuous model updates with feedback loops from threat intelligence systems.
Future of AI in Security Testing Services
AI in Security Testing Services is still in its growth phase. Here’s what’s on the horizon:
lGenerative AI for Test Case Creation: Using models like GPT-4 to simulate attacks and generate intelligent test scripts.
lAutonomous Remediation Agents: AI that not only finds issues but can propose or apply secure code fixes autonomously.
lFederated Threat Learning: Secure sharing of anonymized threat data across organizations to train more resilient models.
lAI-Powered Red Teaming: Simulated human-like attackers that learn and evolve to breach complex systems.
Conclusion
Security is not a checkbox; it’s a continuous journey. As applications grow more complex and the cyber threat landscape expands, relying on traditional methods alone is no longer enough. AI enables Security Testing Services to become proactive, intelligent, and deeply integrated into the development lifecycle.
At Robotico Digital, we’re proud to lead the next generation of Security Testing in Software Testing by harnessing the power of artificial intelligence. Our AI-enhanced services empower organizations to detect vulnerabilities faster, respond more intelligently, and scale their cybersecurity operations with confidence.
0 notes
Text
What Are the Key Considerations When Planning a Fintech Product?

In the rapidly evolving world of finance, fintech software development has emerged as a key driver of innovation, convenience, and accessibility. Whether you're a startup founder or part of a traditional financial institution, developing a fintech product requires more than just technical knowledge—it demands a comprehensive understanding of finance, user behavior, regulatory frameworks, and emerging technologies. To build a successful fintech solution, there are several critical considerations you must address from the very beginning.
1. Understanding the Target Market and Problem Statement
Before writing a single line of code, it's essential to identify your target users and the financial problem you're aiming to solve. Is your product meant to simplify payments, offer better lending options, facilitate investments, or enhance insurance services? Are you targeting millennials, small businesses, rural communities, or enterprise clients?
Defining the problem statement clearly will guide the design and functionality of your product. Additionally, conducting market research helps validate the demand for your solution, assess the competition, and refine your value proposition.
2. Navigating Regulatory and Compliance Requirements
One of the most complex aspects of fintech software development is ensuring full compliance with legal and regulatory requirements. Different countries—and even different states or regions—have specific rules governing digital finance, data storage, user authentication, and financial transactions.
Common regulations include:
KYC (Know Your Customer)
AML (Anti-Money Laundering)
GDPR (for data privacy in the EU)
PCI-DSS (for payment card data security)
Planning your fintech product with compliance in mind from the outset will save time, avoid legal issues, and build trust with your users.
3. Choosing the Right Technology Stack
The technology stack you select forms the foundation of your product’s scalability, performance, and security. Some of the popular technologies used in fintech software development include:
Programming languages like Python, Java, and Kotlin
Frameworks such as React, Node.js, and Spring Boot
Cloud platforms like AWS, Azure, or Google Cloud
Databases like PostgreSQL, MongoDB, and Oracle
The key is to choose technologies that support real-time data processing, high-level security, and easy scalability. Integration with third-party APIs, such as payment gateways, identity verification services, and banking platforms, should also be seamless and secure.
4. Prioritizing Security and Data Protection
Security is at the core of every fintech product. You’re dealing with sensitive user data—bank account numbers, identification details, transaction histories—which makes your platform a potential target for cyberattacks.
Security best practices in fintech include:
End-to-end encryption
Multi-factor authentication (MFA)
Tokenization of payment data
Regular security audits and penetration testing
Role-based access control
Additionally, implementing secure coding practices and training your development team to identify and eliminate vulnerabilities can go a long way in creating a secure fintech environment.
5. User Experience (UX) and Interface Design
No matter how powerful your backend is, a clunky and confusing user interface can drive users away. A clean, intuitive, and responsive interface is critical for adoption and engagement.
Design principles to focus on:
Ease of navigation
Minimalistic yet informative layout
Clear call-to-action buttons
Accessibility for users with disabilities
Consistent branding and visual design
The fintech landscape is extremely competitive, and often, the difference between a successful app and a forgotten one is simply superior UX.
6. Integration with Existing Financial Ecosystems
A successful fintech product often doesn't exist in isolation—it must integrate with existing banking systems, payment processors, credit bureaus, and government portals. These integrations need to be secure, real-time, and capable of handling large transaction volumes.
APIs play a major role here. Your development team should focus on building a flexible architecture that supports third-party API integrations while also allowing easy future enhancements.
7. Scalability and Performance Planning
Fintech products often experience rapid growth—especially if they solve a critical financial problem. Planning for scalability ensures that your infrastructure can handle increasing user loads, transactions, and data volumes without crashing or slowing down.
Cloud-native applications, load balancing, microservices architecture, and automated scaling are essential tools in building a robust and scalable fintech system.
8. Continuous Testing and Feedback Loops
Testing shouldn't be an afterthought. Your development process should include:
Unit testing
Integration testing
User Acceptance Testing (UAT)
Security testing
Performance testing
Once the product is launched, continuous user feedback should be used to improve features, resolve bugs, and refine UX over time. Agile methodologies and DevOps practices can support faster iteration cycles and improved product quality.
9. Cost Management and Development Timelines
Planning your budget and timeline effectively is essential for successful fintech software development. Overruns in either can stall your project or reduce its market competitiveness. Prioritize features using a Minimum Viable Product (MVP) approach and plan for incremental improvements.
10. Partnering with the Right Development Team
Lastly, success in fintech often depends on having the right tech partner. A team that understands both fintech services and the intricacies of the financial industry can bring strategic insights and avoid costly mistakes. For example, Xettle Technologies has built a reputation for delivering secure, scalable, and innovative fintech solutions by combining deep financial expertise with advanced development practices.
Conclusion
Planning a fintech product is a multifaceted process that requires thoughtful strategy, technical excellence, and a deep understanding of user needs and regulations. By considering aspects like compliance, security, scalability, and UX early in the development process, you increase your chances of building a fintech product that not only meets market demands but also leads in innovation and trust.
0 notes
Text
Laabdhi: Your Trusted Accounting Company for Smart Financial Solutions
In today’s fast-paced and highly competitive business environment, accurate financial management is more than a necessity—it's a strategic advantage. This is where Laabdhi, a leading accounting company, plays a vital role. Renowned for its precision, professionalism, and personalized service, Laabdhi has become a trusted name among businesses looking to streamline their finances and achieve long-term growth.
Founded with a vision to simplify complex accounting processes, Laabdhi offers a full spectrum of financial services, including bookkeeping, tax planning, payroll, compliance, and CFO-level advisory. Whether you’re a startup looking for basic financial setup or a large enterprise seeking end-to-end accounting support, Laabdhi’s customized approach ensures that every client gets the attention and expertise they deserve.
One of Laabdhi’s strongest advantages lies in its deep understanding of diverse industries. With clients spanning sectors like manufacturing, retail, IT, healthcare, logistics, and e-commerce, the company brings industry-specific insights to every engagement. This allows them to not only ensure regulatory compliance but also identify cost-saving opportunities and provide data-driven financial strategies.
Technology is at the heart of Laabdhi’s operations. As a modern accounting company, Laabdhi uses the latest cloud-based accounting tools and software, ensuring accuracy, real-time reporting, and easy access to financial data. By automating repetitive tasks and integrating powerful analytics, Laabdhi helps businesses reduce human error, save time, and make informed decisions faster.
What truly sets Laabdhi apart is its client-first philosophy. The team prides itself on building strong relationships based on transparency, integrity, and clear communication. Every client is assigned a dedicated account manager, making it easy to discuss financial goals, ask questions, and receive timely updates. This hands-on approach has earned Laabdhi a loyal clientele and a reputation for exceptional service.
For businesses expanding internationally or managing multi-location operations, Laabdhi also offers outsourced accounting services. With an experienced team well-versed in global accounting standards such as GAAP and IFRS, the company ensures smooth financial operations across borders. Their offshore delivery model helps companies save significantly on operational costs while maintaining high standards of quality and compliance.
Another key strength is Laabdhi’s focus on taxation and regulatory compliance. The ever-changing tax landscape can be overwhelming for businesses, but Laabdhi’s experts stay ahead of updates and legislative changes. From income tax and GST filings to audit support and international tax advisory, they ensure that clients remain compliant while optimizing their tax liability.
In conclusion, if you’re searching for a reliable and forward-thinking accounting company, Laabdhi should be at the top of your list. With its strong technical expertise, industry knowledge, and commitment to client success, Laabdhi empowers businesses to focus on growth while leaving the numbers to the experts. From daily bookkeeping to strategic financial planning, Laabdhi delivers smart solutions that drive real results.
0 notes
Text
Automation and Integration Needs Power Robust Growth in System Integrator Market
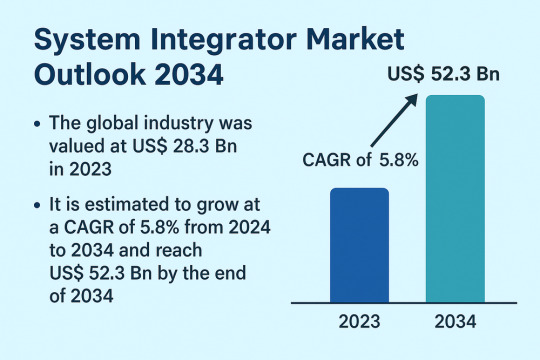
The global System Integrator Market is poised for significant growth, projected to rise from US$ 28.3 Bn in 2023 to US$ 52.3 Bn by 2034, growing at a CAGR of 5.8% from 2024 to 2034. This growth is driven by the widespread adoption of industrial robots, technological advancements, and a pressing need among businesses to optimize operational efficiencies through connected systems.
System integrators play a pivotal role in designing, implementing, and maintaining integrated solutions that bring together hardware, software, and consulting services. These services support organizations in unifying internal and external systems, such as SCADA, HMI, MES, PLC, and IIoT, to enable seamless data flow and system interoperability.
Market Drivers & Trends: One of the primary market drivers is the rise in adoption of industrial robots. As industries accelerate automation, robotic system integrators have become vital in delivering customized, scalable, and high-performing solutions tailored to complex manufacturing needs.
Another major catalyst is the surge in technological advancements. Integrators are deploying cloud-based tools and platforms that provide real-time data insights, improve developer productivity, and support hybrid architectures. The increasing use of Artificial Intelligence (AI), Machine Learning (ML), and Internet of Things (IoT) in integration solutions is fostering innovation and growth.
Latest Market Trends
Several emerging trends are shaping the system integrator landscape:
Cloud modernization platforms such as IBM’s Z and Cloud Modernization Center are enabling businesses to accelerate the transition to hybrid cloud environments.
Modular automation platforms are gaining popularity, allowing companies to rapidly deploy and scale integration solutions across multiple industry verticals.
Edge computing and cybersecurity solutions are increasingly being integrated to support secure, real-time decision-making on the production floor.
Digital hubs and scalable workflow engines are being adopted by integrators to support multi-specialty applications with high adaptability.
Key Players and Industry Leaders
The system integrator market is characterized by a strong mix of global leaders and regional specialists. Key players include:
ATS Corporation
Avanceon
Avid Solutions
Brock Solutions
JR Automation
MAVERICK Technologies, LLC
Burrow Global, LLC
BW Design Group
John Wood Group PLC
TESCO CONTROLS
These companies are actively investing in next-generation technologies, enhancing their product portfolios, and pursuing strategic acquisitions to strengthen market presence. For instance, in July 2023, ATS Corporation acquired Yazzoom BV, a Belgian AI and ML solutions provider, expanding their capabilities in smart manufacturing.
Recent Developments
Olympus Corporation launched the EASYSUITE ES-IP system in July 2023 in the U.S., offering advanced visualization and integration solutions for procedure rooms.
IBM introduced key updates in 2021 and 2022 to streamline mission-critical application modernization using cloud services and hybrid IT strategies.
Asia-Pacific companies have led the charge in deploying advanced integrated systems, reflecting the rapid industrial digitization in countries such as China, Japan, and South Korea.
Market Opportunities
Opportunities abound in both mature and emerging markets:
Smart factories and Industry 4.0 transformation offer immense potential for integrators to offer comprehensive solutions tailored to real-time analytics, predictive maintenance, and remote monitoring.
Government-led infrastructure modernization projects, particularly in Asia and the Middle East, are increasing demand for integrated control systems and plant asset management solutions.
The energy transition movement, including renewables and electrification of industrial processes, requires new types of integration across decentralized assets.
Future Outlook
As industries pursue digital transformation, the role of system integrators will evolve from traditional project implementers to long-term strategic partners. The future will see increasing demand for intelligent automation, cross-domain expertise, and real-time adaptive solutions. Vendors who can provide holistic, secure, and scalable services will dominate the landscape.
With continued advancements in AI, IoT, and robotics, the system integrator market will continue to thrive, transforming operations across diverse sectors, from automotive and food & beverages to oil & gas and pharmaceuticals.
Review critical insights and findings from our Report in this sample - https://www.transparencymarketresearch.com/sample/sample.php?flag=S&rep_id=82550
Market Segmentation
The market is segmented based on offering, technology, and end-use industry.
By Offering:
Hardware
Software
Service (Consulting, Design, Installation)
By Technology:
Human-Machine Interface (HMI)
Supervisory Control and Data Acquisition (SCADA)
Manufacturing Execution System (MES)
Functional Safety System
Machine Vision
Industrial Robotics
Industrial PC
Industrial Internet of Things (IIoT)
Machine Condition Monitoring
Plant Asset Management
Distributed Control System (DCS)
Programmable Logic Controller (PLC)
By End-use Industry:
Oil & Gas
Chemical & Petrochemical
Food & Beverages
Automotive
Energy & Power
Pharmaceutical
Pulp & Paper
Aerospace
Electronics
Metals & Mining
Others
Regional Insights
Asia Pacific leads the global system integrator market, holding the largest market share in 2023. This leadership is attributed to:
Rapid industrialization and digital transformation in China, Japan, and India.
Strong investments in smart manufacturing and Industry 4.0 initiatives.
Government support for infrastructure modernization, especially through Smart City programs and cybersecure IT frameworks.
North America and Europe also show strong demand, driven by the presence of established manufacturing facilities and a robust focus on sustainable operations and green automation.
Why Buy This Report?
Comprehensive Market Analysis: Deep insights into market size, share, and growth across all major segments and geographies.
Detailed Competitive Landscape: Profiles of leading companies with analysis of their strategy, product offerings, and key financials.
Actionable Intelligence: Understand technological trends, regulatory developments, and investment opportunities.
Forecast-Based Strategy: Develop long-term strategic plans using data-driven forecasts up to 2034.
Frequently Asked Questions (FAQs)
1. What is the projected value of the system integrator market by 2034? The global system integrator market is projected to reach US$ 52.3 Bn by 2034.
2. What is the current CAGR for the forecast period 2024–2034? The market is anticipated to grow at a CAGR of 5.8% during the forecast period.
3. Which region holds the largest market share? Asia Pacific dominated the global market in 2023 and is expected to continue leading due to rapid industrialization and technology adoption.
4. What are the key growth drivers? Key drivers include the rise in adoption of industrial robots and continuous advancements in integration technologies like IIoT, AI, and cloud platforms.
5. Who are the major players in the system integrator market? Prominent players include ATS Corporation, JR Automation, Brock Solutions, MAVERICK Technologies, and Control Associates, Inc.
6. Which industries are adopting system integrator services the most? High adoption is seen in industries such as automotive, oil & gas, food & beverages, pharmaceuticals, and electronics.
Explore Latest Research Reports by Transparency Market Research:
Multi-Mode Chipset Market: https://www.transparencymarketresearch.com/multi-mode-chipset-market.html
Accelerometer Market: https://www.transparencymarketresearch.com/accelerometer-market.html
Luminaire and Lighting Control Market: https://www.transparencymarketresearch.com/luminaire-lighting-control-market.html
Advanced Marine Power Supply Market: https://www.transparencymarketresearch.com/advanced-marine-power-supply-market.html
About Transparency Market Research Transparency Market Research, a global market research company registered at Wilmington, Delaware, United States, provides custom research and consulting services. Our exclusive blend of quantitative forecasting and trends analysis provides forward-looking insights for thousands of decision makers. Our experienced team of Analysts, Researchers, and Consultants use proprietary data sources and various tools & techniques to gather and analyses information. Our data repository is continuously updated and revised by a team of research experts, so that it always reflects the latest trends and information. With a broad research and analysis capability, Transparency Market Research employs rigorous primary and secondary research techniques in developing distinctive data sets and research material for business reports. Contact: Transparency Market Research Inc. CORPORATE HEADQUARTER DOWNTOWN, 1000 N. West Street, Suite 1200, Wilmington, Delaware 19801 USA Tel: +1-518-618-1030 USA - Canada Toll Free: 866-552-3453 Website: https://www.transparencymarketresearch.com Email: [email protected]
0 notes
Text
The Ultimate Ransomware Defense Guide in 2025

Ransomware: the digital plague that continues to evolve, terrorize businesses, and cost billions globally. In 2025, it's not just about encrypting files anymore; it's about sophisticated double (and even triple) extortion, AI-powered phishing campaigns, supply chain attacks, and leveraging advanced techniques to bypass traditional defenses. The threat landscape is more complex and dangerous than ever.
While no defense is absolutely foolproof, building a layered, proactive, and continuously adapting cybersecurity posture is your ultimate weapon against ransomware. This guide outlines the essential pillars of defense for the year ahead.
1. Fortify the "Human Firewall" with Advanced Security Awareness
The unfortunate truth is that often, the easiest way into an organization is through its people. Human error, social engineering, and a lack of awareness remain primary vectors for ransomware infections.
Beyond Basic Training: Move beyond generic "don't click suspicious links." Implement AI-driven, adaptive phishing simulations that mimic real-world, personalized threats (e.g., deepfake voice phishing or highly convincing AI-generated emails).
Continuous & Engaging Education: Foster a pervasive security-first culture. Integrate bite-sized security tips into daily workflows, use gamified learning platforms, and celebrate employees who successfully identify and report threats.
Rapid Reporting Mechanisms: Empower employees to be your first line of defense. Ensure they know what to report and how to do it quickly, with no fear of reprisal. A swift report can be the difference between an isolated incident and a full-blown crisis.
2. Embrace a Robust Zero Trust Architecture (ZTA)
The perimeter-based security model is dead. In 2025, assume breach and "never trust, always verify" is the golden rule.
Micro-segmentation: Isolate critical systems and data within your network. If one segment is compromised, ransomware cannot easily spread laterally to other areas, dramatically reducing the potential blast radius.
Least Privilege Access: Grant users and applications only the absolute minimum access required to perform their functions. Even if an account is compromised, its limited permissions will restrict what a ransomware attacker can do.
Adaptive Authentication & Continuous Verification: Implement Multi-Factor Authentication (MFA) across all accounts, especially privileged ones. Beyond that, use adaptive authentication that continuously verifies user and device trust based on context (location, device health, behavioral patterns) rather than just a one-time login.
3. Leverage Advanced Endpoint & Network Security (XDR/NDR)
Your endpoints (laptops, servers, mobile devices) and network traffic are prime targets and crucial detection points.
Extended Detection and Response (XDR): Move beyond traditional Endpoint Detection and Response (EDR). XDR unifies and correlates telemetry from endpoints, network, cloud, email, and identity layers. This comprehensive view, powered by AI and machine learning, allows for faster detection of subtle ransomware indicators, automated threat hunting, and rapid containment across your entire digital estate.
Network Detection and Response (NDR): Continuously monitor all network traffic for anomalous patterns, unauthorized communications (e.g., C2 callbacks), and data exfiltration attempts. NDR can spot the tell-tale signs of ransomware preparation and execution as it tries to communicate or spread.
Cloud Security Posture Management (CSPM): For organizations leveraging cloud environments, CSPM continuously checks for misconfigurations (like publicly exposed storage buckets or overly permissive cloud functions) that ransomware gangs actively seek to exploit for initial access or data exfiltration.
4. Implement Impeccable, Immutable Backups
If all else fails, a clean backup is your ultimate get-out-of-jail-free card. But traditional backups are often targeted by ransomware.
The 3-2-1-1-0 Rule: Maintain at least 3 copies of your data, on 2 different media types, with 1 copy offsite, 1 copy offline or immutable, and 0 errors after verification.
Immutable Backups: This is critical for 2025. Ensure a significant portion of your backups are truly immutable – meaning they cannot be altered, encrypted, or deleted by any means for a defined period. This "air-gapped" or logically separated copy ensures you always have an uncorrupted source for recovery, even if your live environment and other backups are compromised.
Regular Testing: Backups are useless if they don't work. Conduct frequent, rigorous tests of your entire backup and recovery process to ensure data integrity and demonstrate your ability to restore operations quickly.
5. Proactive Vulnerability Management & Incident Readiness
Prevention is ideal, but preparation for a breach is non-negotiable.
Continuous Vulnerability Management: Regularly scan for and prioritize vulnerabilities across your entire IT estate, including applications, operating systems, network devices, and cloud configurations. Automate patching and configuration hardening for known exploits, as these are often ransomware's entry points.
Penetration Testing & Red Teaming: Don't wait for attackers to find your weaknesses. Regularly hire ethical hackers to simulate real-world ransomware attacks against your systems, testing your technical controls and your team's response capabilities.
Robust Incident Response Plan (IRP): Develop a detailed, well-documented IRP specifically for ransomware attacks. This plan should clearly define roles, responsibilities, communication protocols (internal, external, legal, PR), and step-by-step procedures for containment, eradication, recovery, and post-incident analysis. Practice this plan regularly through tabletop exercises.
In 2025, ransomware is a dynamic and relentless adversary. Defeating it requires moving beyond siloed security solutions to a holistic, continuously evolving strategy that encompasses people, processes, and cutting-edge technology. By embedding these principles into your organizational DNA, you can significantly enhance your resilience and ensure that even if ransomware knocks, it won't be able to get in and hold your business hostage.
0 notes